1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
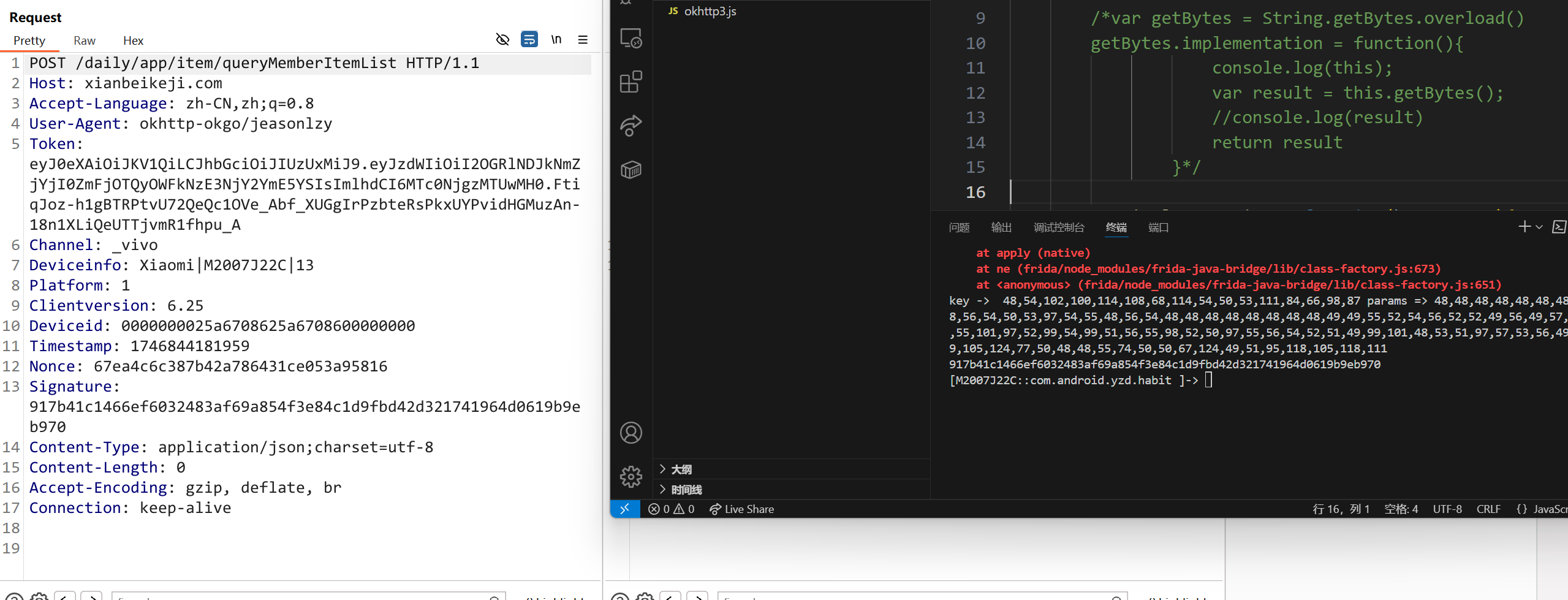
| import hmac
import hashlib
import requests
import json
import time
import uuid
def getSignature(headers, data):
param_list = []
param_list.append(headers['Channel'])
param_list.append(headers['Deviceinfo'])
param_list.append(headers['Deviceid'])
param_list.append(headers['Clientversion'])
param_list.append(headers['Nonce'])
param_list.append(headers['Platform'])
param_list.append(headers['Timestamp'])
param_list.append(data)
param_list.sort()
param_str = ''.join(str(item) for item in param_list)
key = b"06fdrlDr625oTBbW"
message = (param_str).encode()
hmac_sha256 = hmac.new(key, message, hashlib.sha256)
return hmac_sha256.hexdigest()
headers = {
'Accept-Language': 'zh-CN,zh;q=0.8',
'User-Agent': 'okhttp-okgo/jeasonlzy',
'Channel': '_vivo',
'Deviceinfo': 'Xiaomi|M2007J22C|13',
'Platform': '1',
'Clientversion': '6.25',
'Deviceid': '0000000025a6708625a6708600000000',
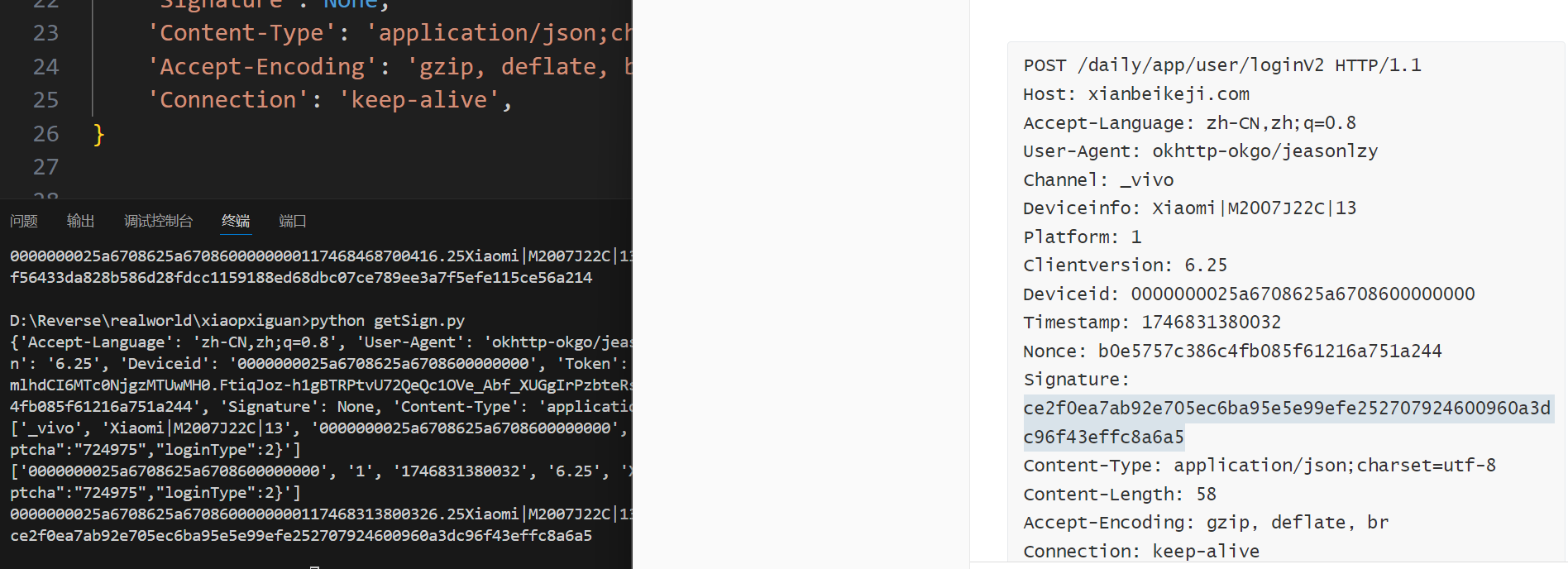
'Token': 'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJzdWIiOiI2OGRlNDJkNmZjYjI0ZmFjOTQyOWFkNzE3NjY2YmE5YSIsImlhdCI6MTc0NjgzMTUwMH0.FtiqJoz-h1gBTRPtvU72QeQc1OVe_Abf_XUGgIrPzbteRsPkxUYPvidHGMuzAn-18n1XLiQeUTTjvmR1fhpu_A',
'Timestamp': str(int(time.time())),
'Nonce': str(uuid.uuid4()).replace("-", ""),
'Signature': None,
'Content-Type': 'application/json;charset=utf-8',
'Accept-Encoding': 'gzip, deflate, br',
'Connection': 'keep-alive',
}
data = {
"activeCode": "1919810"
}
data = json.dumps(data).replace(" ", "")
Signature = getSignature(headers, data)
print(Signature)
headers['Signature'] = Signature
url = 'https://xianbeikeji.com/daily/app/user/exchangeActiveCode'
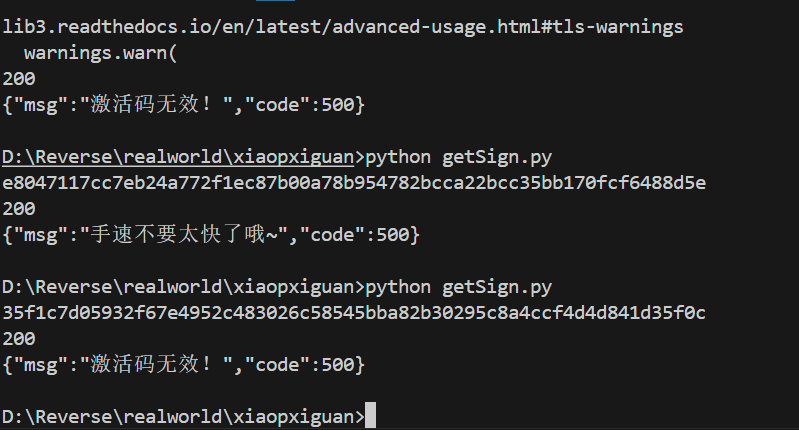
response = requests.post(url, headers=headers, data=data)
print(response.status_code)
print(response.text)
|