某React Native Hermes的APP逆向分析
抓包
抓包,对登录接口进行分析

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
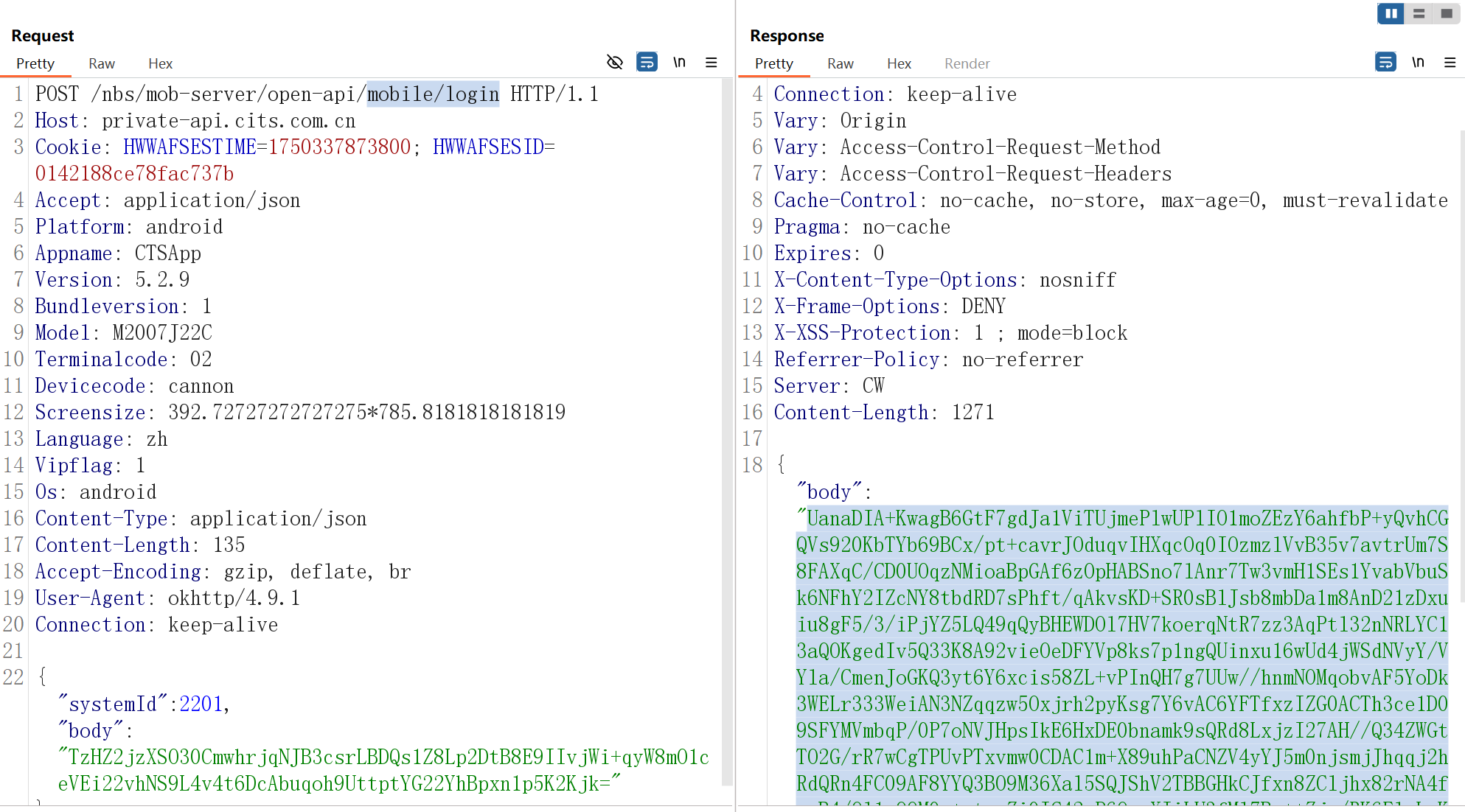
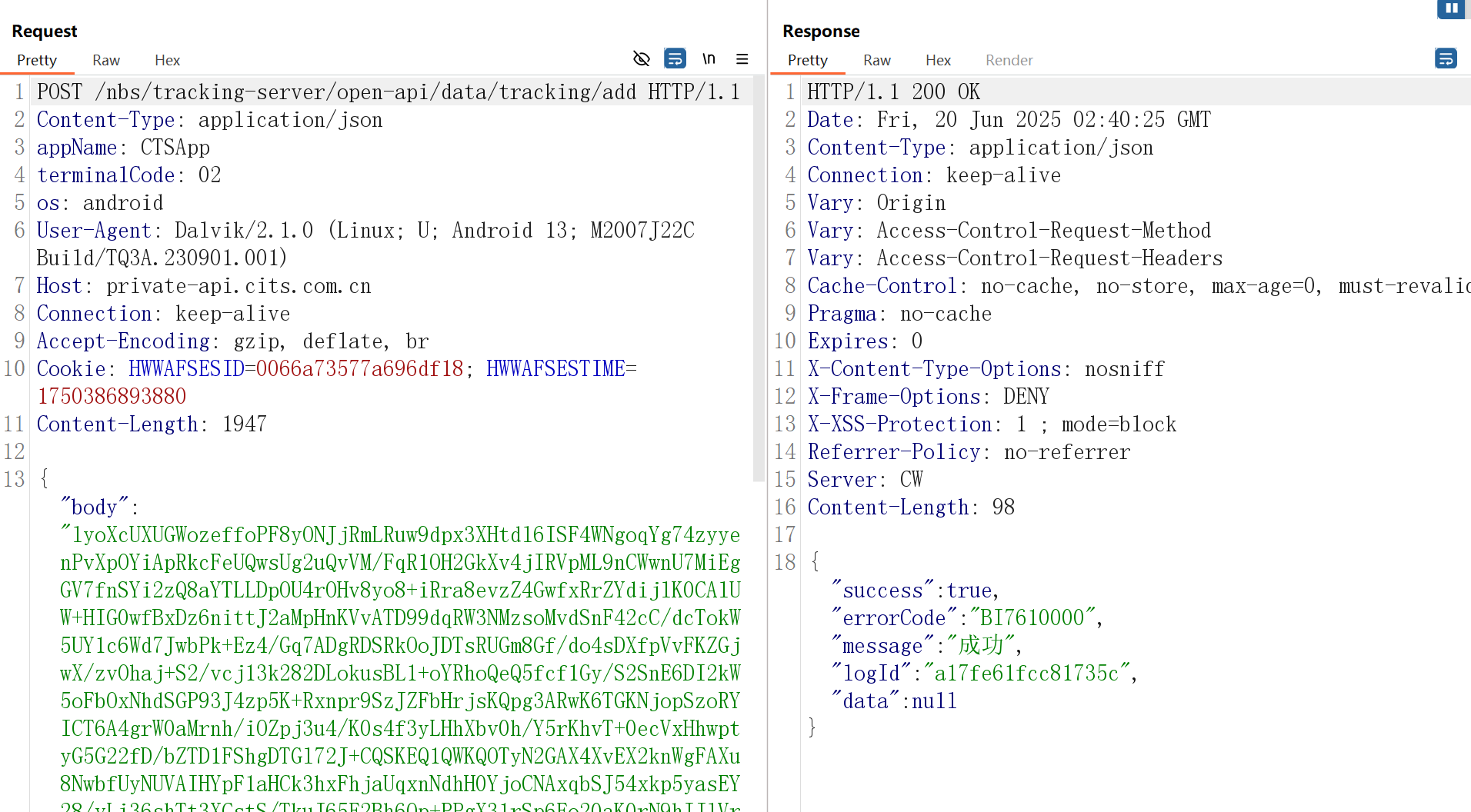
| POST /nbs/mob-server/open-api/mobile/login HTTP/1.1
Host: private-api.cits.com.cn
Cookie: HWWAFSESTIME=1750337873800; HWWAFSESID=0142188ce78fac737b
Accept: application/json
Platform: android
Appname: CTSApp
Version: 5.2.9
Bundleversion: 1
Model: M2007J22C
Terminalcode: 02
Devicecode: cannon
Screensize: 392.72727272727275*785.8181818181819
Language: zh
Vipflag: 1
Os: android
Content-Type: application/json
Content-Length: 135
Accept-Encoding: gzip, deflate, br
User-Agent: okhttp/4.9.1
Connection: keep-alive
{"systemId":2201,"body":"TzHZ2jzXSO30CmwhrjqNJB3csrLBDQs1Z8Lp2DtB8E9IIvjWi+qyW8mO1ceVEi22vhNS9L4v4t6DcAbuqoh9UttptYG22YhBpxn1p5K2Kjk="}
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| HTTP/1.1 200 OK
Date: Fri, 20 Jun 2025 02:40:38 GMT
Content-Type: application/json
Connection: keep-alive
Vary: Origin
Vary: Access-Control-Request-Method
Vary: Access-Control-Request-Headers
Cache-Control: no-cache, no-store, max-age=0, must-revalidate
Pragma: no-cache
Expires: 0
X-Content-Type-Options: nosniff
X-Frame-Options: DENY
X-XSS-Protection: 1 ; mode=block
Referrer-Policy: no-referrer
Server: CW
Content-Length: 1271
{"body":"UanaDIA+KwagB6GtF7gdJa1ViTUjmePlwUPlIO1moZEzY6ahfbP+yQvhCGQVs920KbTYb69BCx/pt+cavrJOduqvIHXqcOq0IOzmzlVvB35v7avtrUm7S8FAXqC/CD0UOqzNMioaBpGAf6zOpHABSno7lAnr7Tw3vmH1SEs1YvabVbuSk6NFhY2IZcNY8tbdRD7sPhft/qAkvsKD+SR0sBlJsb8mbDa1m8AnD21zDxuiu8gF5/3/iPjYZ5LQ49qQyBHEWDOl7HV7koerqNtR7zz3AqPtl32nNRLYC13aQOKgedIv5Q33K8A92vieOeDFYVp8ks7p1ngQUinxu16wUd4jWSdNVyY/VYla/CmenJoGKQ3yt6Y6xcis58ZL+vPInQH7g7UUw//hnmNOMqobvAF5YoDk3WELr333WeiAN3NZqqzw5Oxjrh2pyKsg7Y6vAC6YFTfxzIZG0ACTh3ce1D09SFYMVmbqP/0P7oNVJHpsIkE6HxDE0bnamk9sQRd8LxjzI27AH//Q34ZWGtTO2G/rR7wCgTPUvPTxvmw0CDAC1m+X89uhPaCNZV4yYJ5m0njsmjJhqqj2hRdQRn4FC09AF8YYQ3BO9M36Xal5SQJShV2TBBGHkCJfxn8ZCljhx82rNA4fwuB4/Ol1sQOM0u+rtwpZi0IC42rP6OuqXIiLU3fMl7Bp++Zju/RK6ElwLyKRf80mi1yz7g0zHbb1HXYHJQeSNPl2RkH3C7w36xwdR+cjaFZskDLJSDjDDAvrCUb7ajw+sxPJdAAee6JvPhsbRPHHeooPR8fjyjft2synYH4kk56Ny6EfGH/7j/zrj7LOlZJbLW+otc0aNn5xn+LgR+53q3DiYzyHEqdCBqKfaVN3JHLb/vNImmcr9e1GGKQ+vuByttg1AfR4R8+169Z+94l65Mg/RxHcH9wCli7VTW5jKuKYDLEL8Yf2l14rfYfy35yA3Raf8F1ygt78ubo+nxx5Z99R42RhiEOpNm9OKMhBG4V4VwXchrP7HNZmst77hGAoMfN/hyltp0i7HhpAanmOCi3JkwRtk4xcNicKIZvRCmwDCskvXAkPeUTJbRzTzuVuIY456r4lmOnkDc5d2fBuKmvCByctI0SxqbdAKeTwvu5bgNN2Nx4Y+zB/7t2eTyxYcEQk3CKvj/d5AFFT/AhWtGEwD/mRmy91HY0Ddi7EsCurkdzM4OXtW3YpgRArIL7aJbnnyMK0pB9K7pMOcRyFl0AOVgbsuujAfJI="}
|
算法定位
无壳无检测
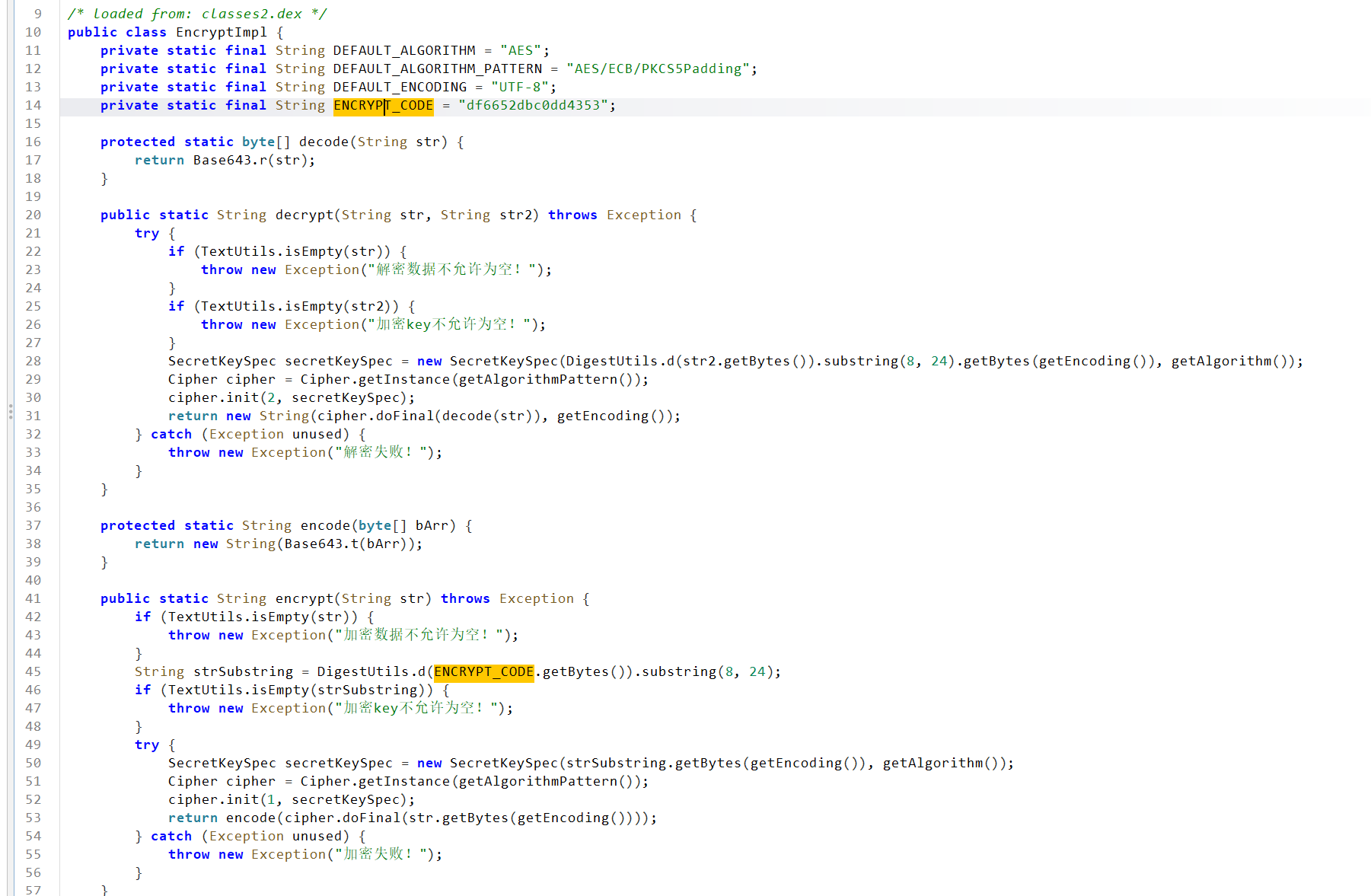
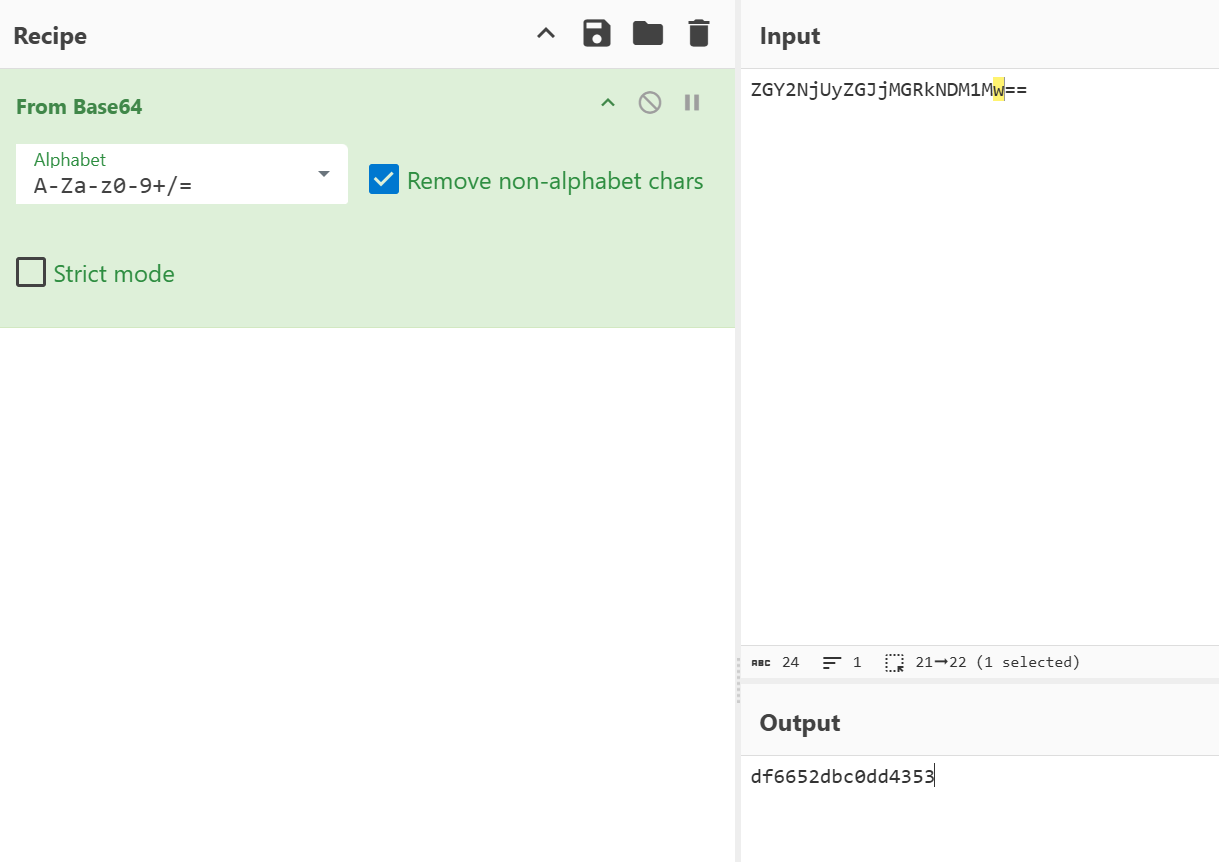
使用自吐脚本,发现一处调用AES_ECB加密,key 为f47a08b62bd90309

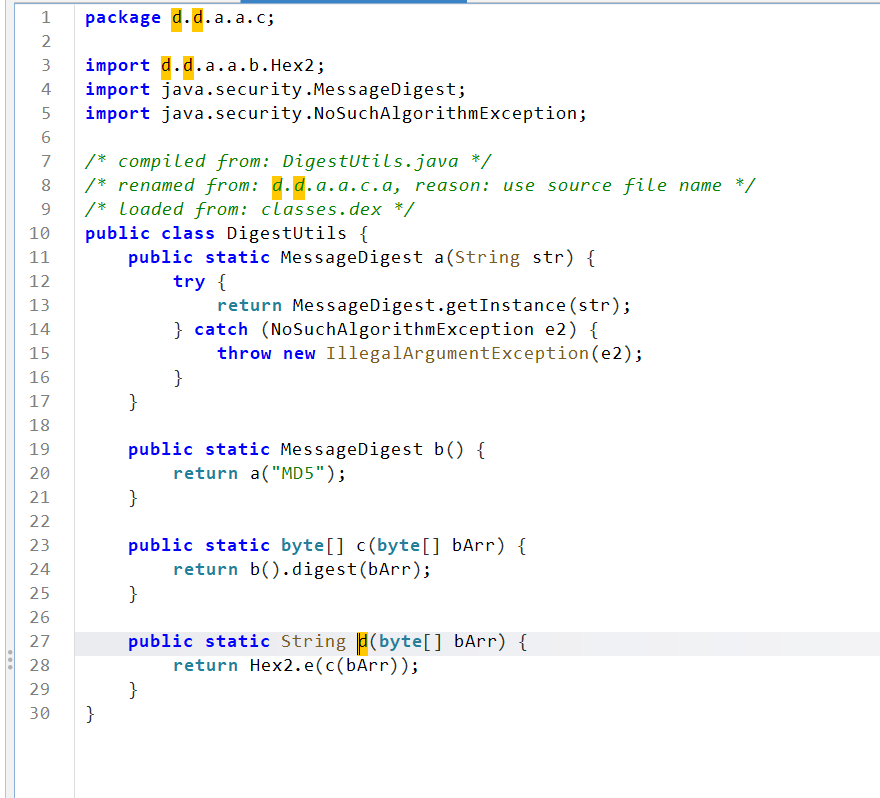
key是通过ENCRYPT_CODE进行小写md5后,截取[8, 24]位的字符

但是接着发现,,虽然该key能够解出请求的数据,但无法解密响应的数据

而且经过分析,虽然app走了该encrypt函数,但其发包函数对应的压根就不是这条登录流量
而是名为data/tracking/add的api,并没有什么用

java层完全找不到更多相关的类
React Native Hermes分析
尝试搜索一波api字符串,发现只出现在index.android.bundle

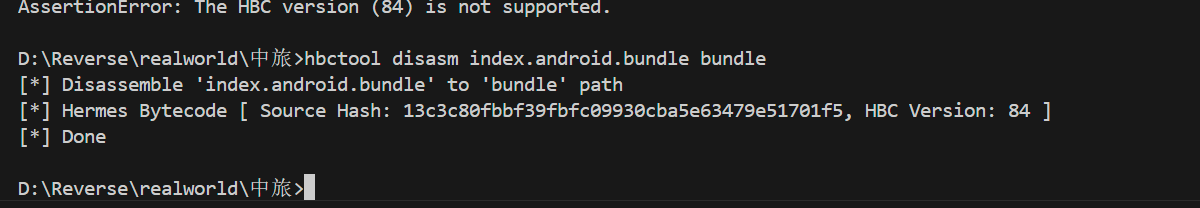
上网搜一下,发现是React Native Hermes,使用hbc-v84将其转化为Hermes字节码
niosega/hbctool at draft/hbc-v84

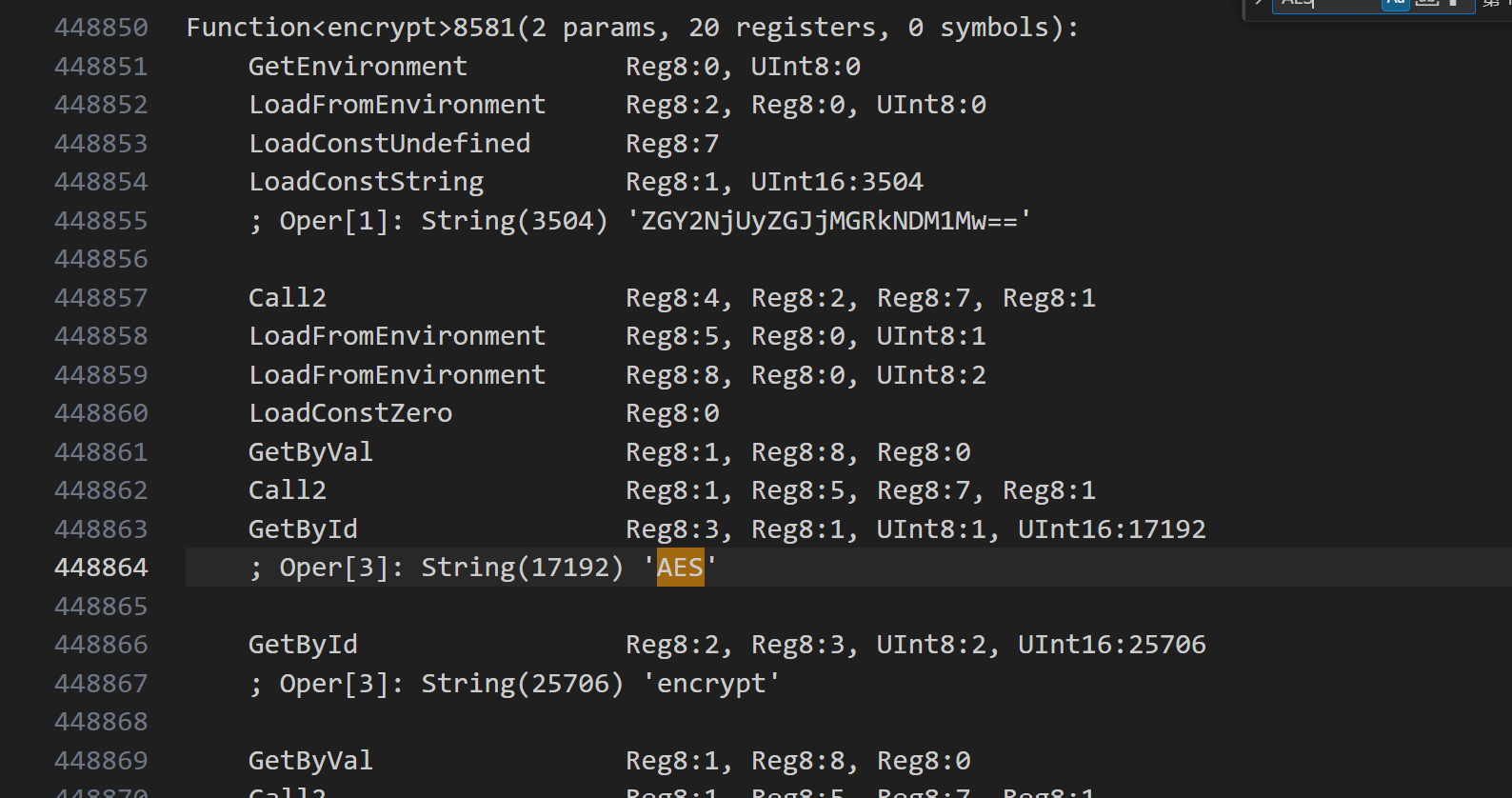
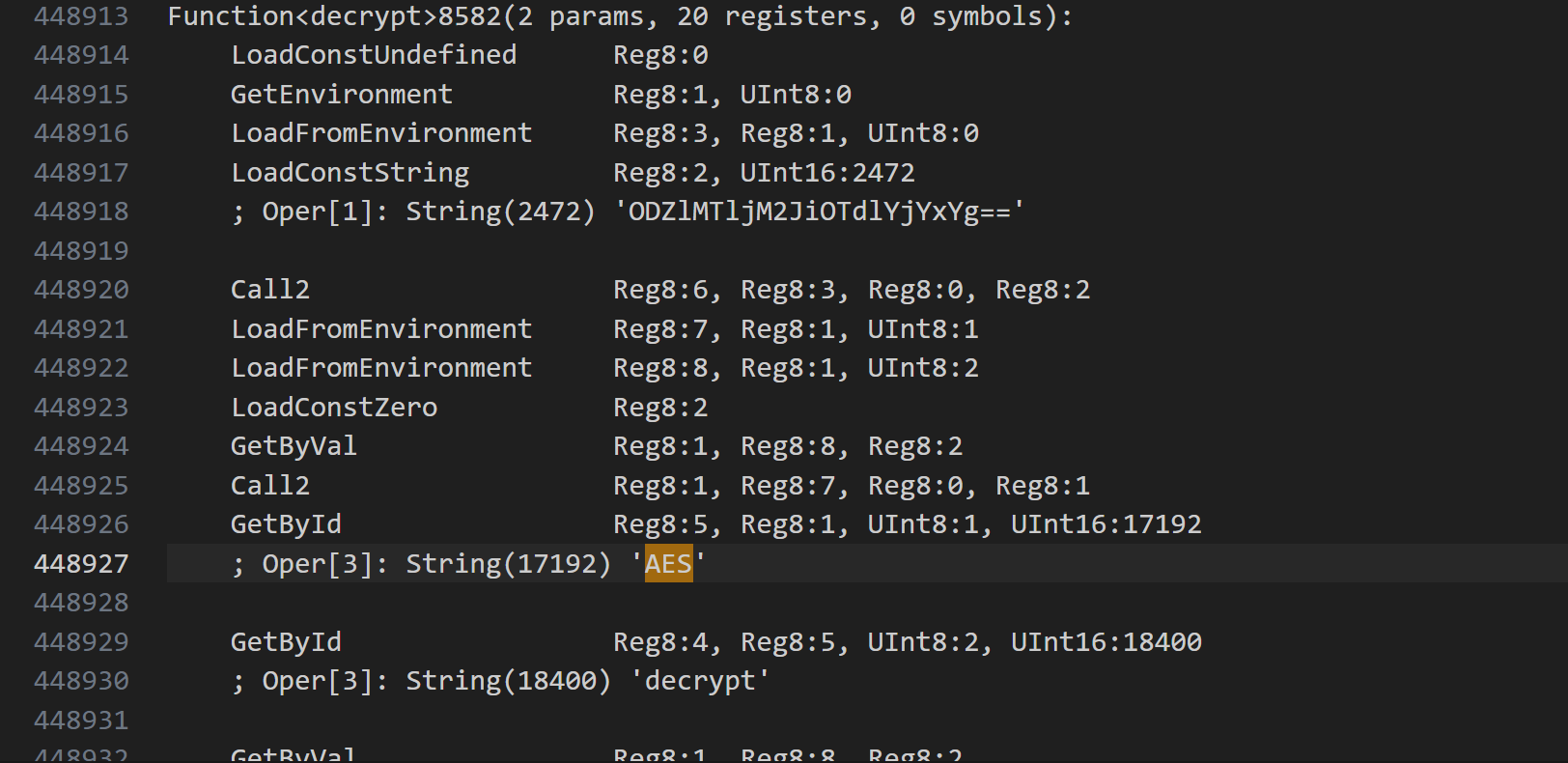
搜素AES方法,发现encrypt函数,并有一串base64字符

解出来发现就是EncryptImpl类中的ENCRYPT_CODE,那么猜测就是经过相同的变化

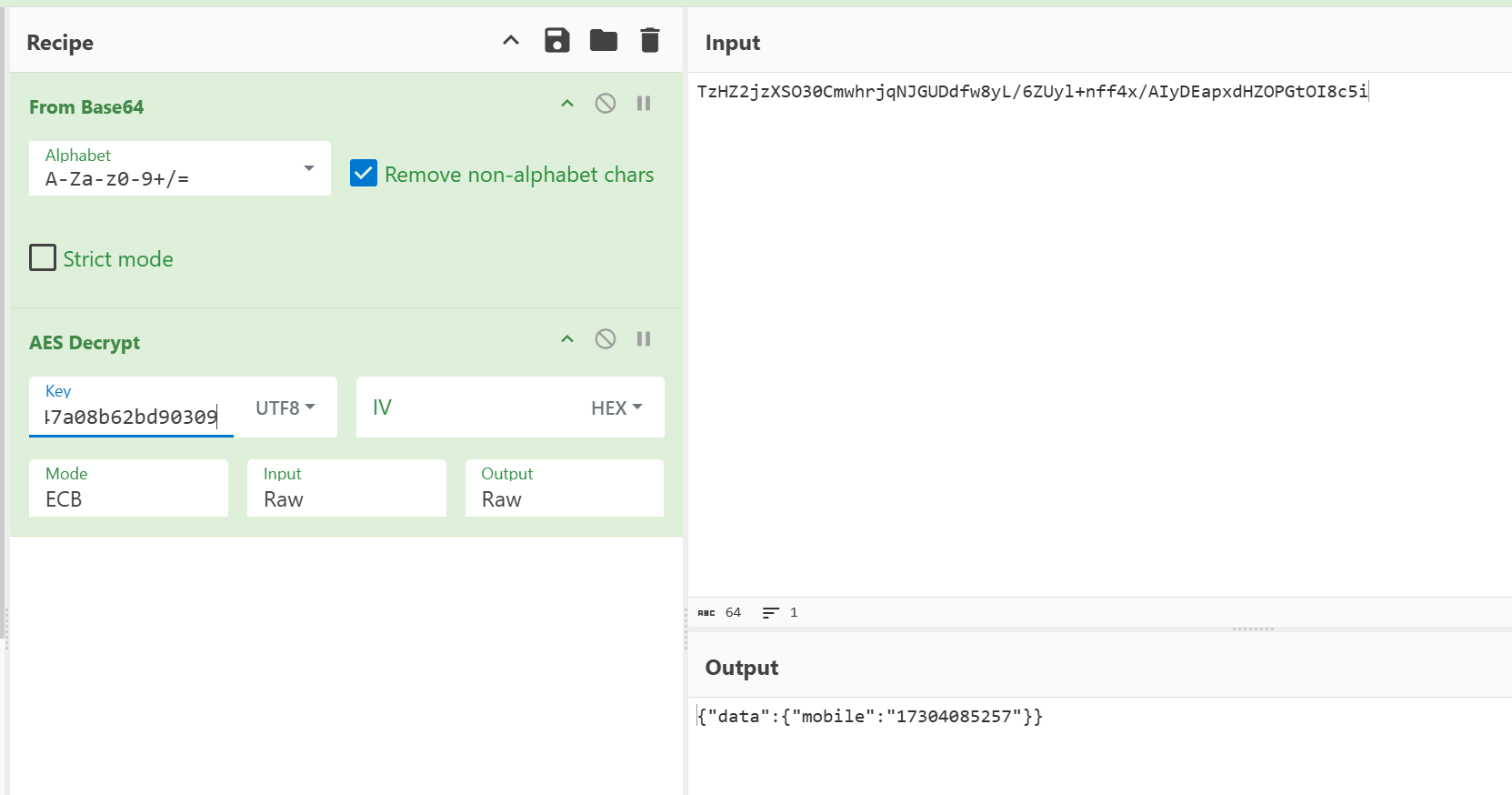
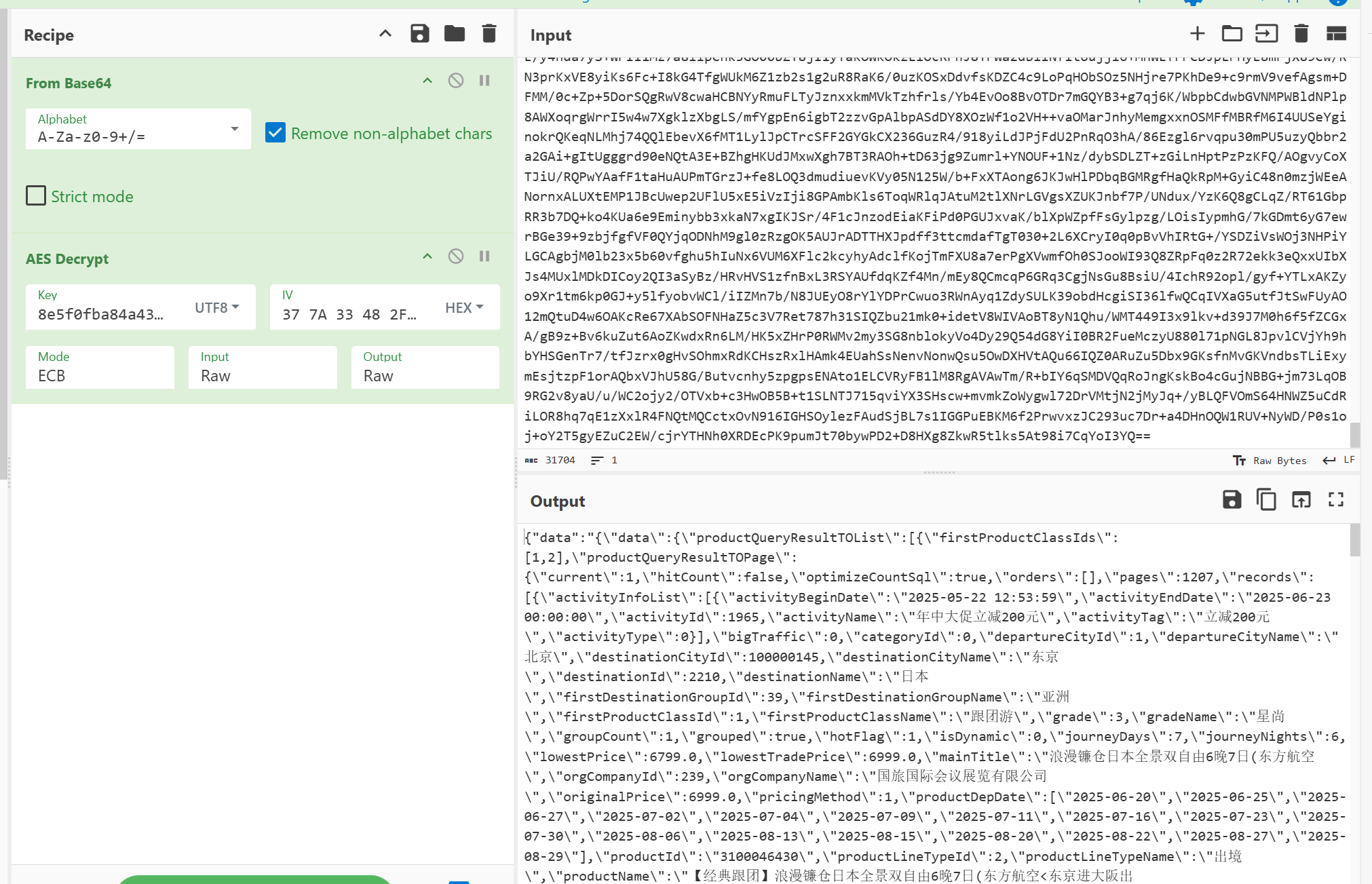
接着拿到解密的ENCRYPT_CODE,并得到key为8e5f0fba84a43988

解密响应成功