强网拟态2025初赛 Mobile方向just Writeup
just
前言:
白天打ycb决赛,晚上9点多才回到酒店开做,后面有点头昏眼花,还好最后也是出了
运行环境(可正常运行APP):
Android13 (lineageOS 20)
jadx打开,发现是Unity il2cpp写的app,(可以立马关闭jadx了)
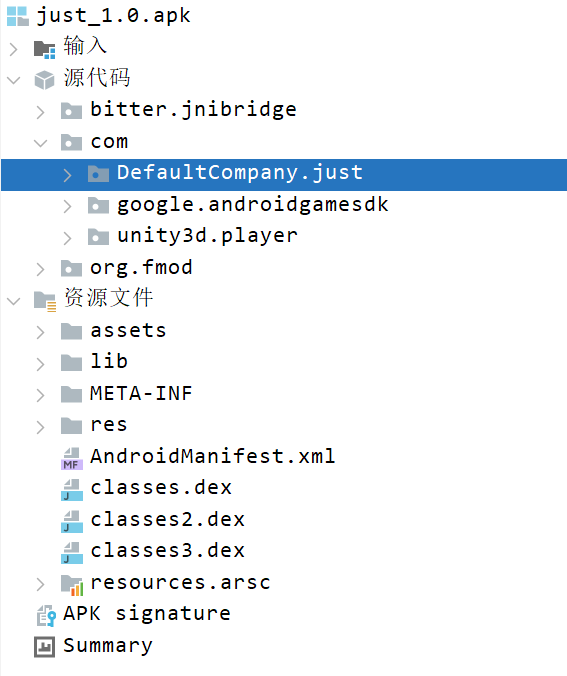
一开始尝试Il2CppDumper失败
后面可以发现libil2cpp.so和global-metadata.dat都被加密
libil2cpp.so明显不具备elf结构
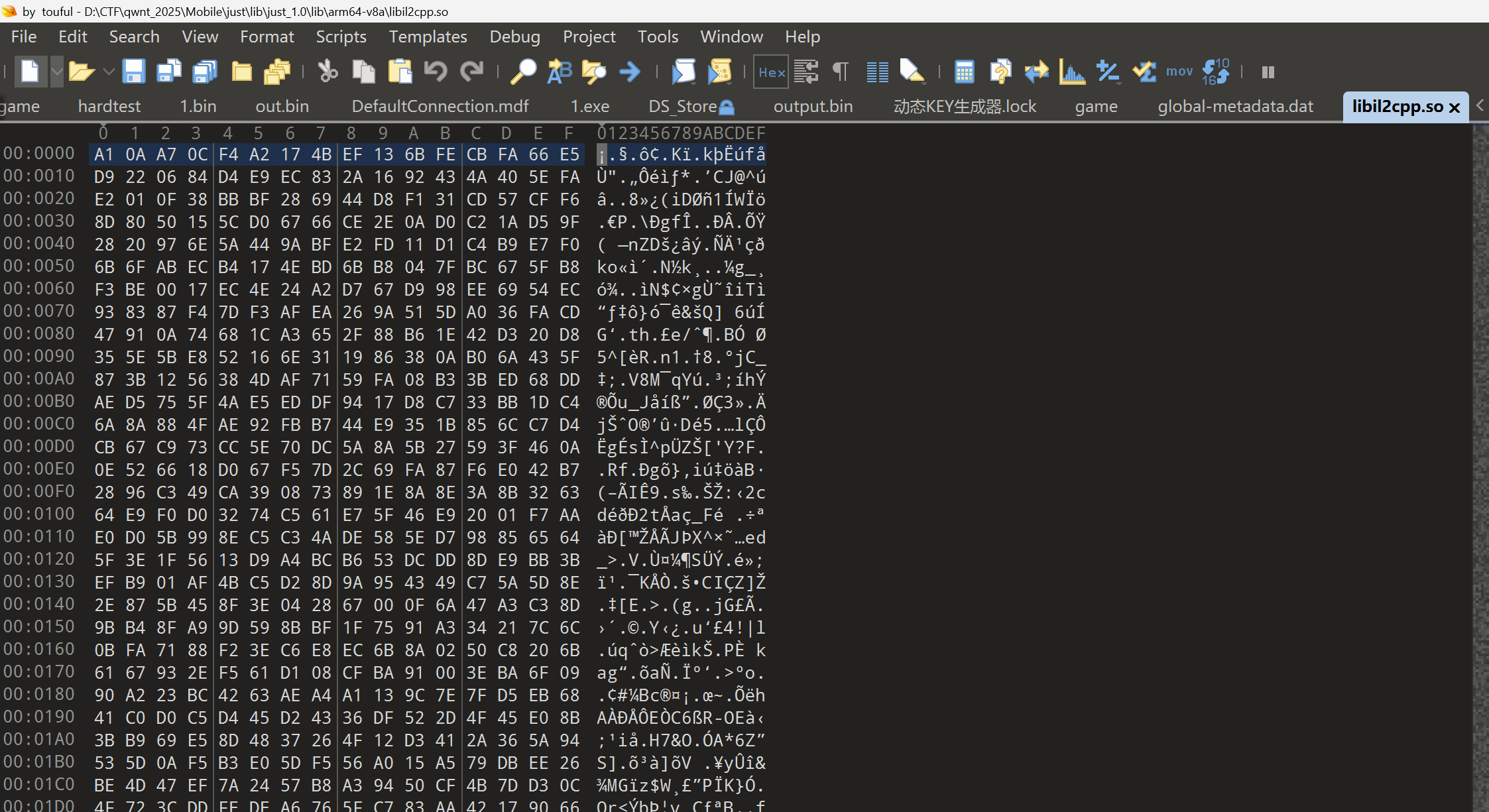
global-metadata.dat从0x400开始被加密

一开始想用frida-il2cpp-bridge做,但libjust.so中有反调试,frida检测和crc校验等
frida注入直接被杀,而且第一次检测到后,除非重启手机,否则都会被杀
下面是frida的过检测脚本
1 | function nop_64(addr) { |
但这样frida-il2cpp-bridge还是无法正常使用,那就只能尝试别的方法了

程序使用了dobbyHook框架对android_dlopen_ext和dlopen函数进行了hook
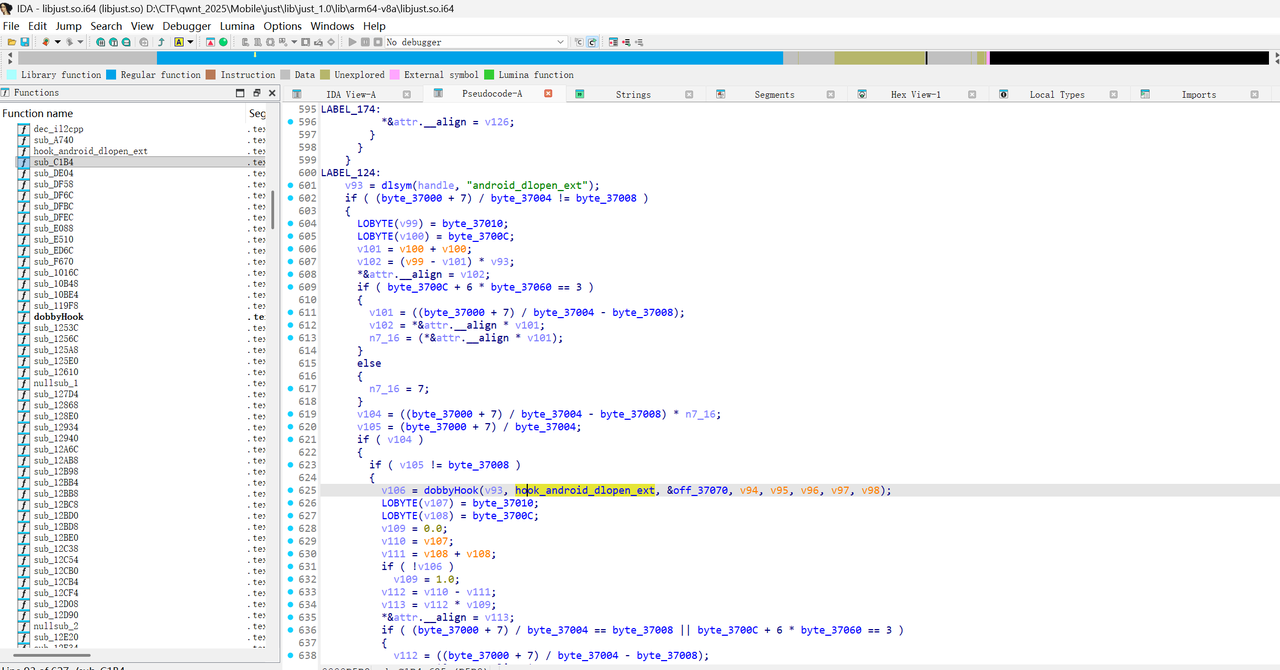
这边应该是检测到加载的so为libil2cpp.so且文件被加密(因为我后面将解密好的so重打包发现能正常运行)才解密的流程

解密部分就是一个rc4的解密

cyberchef直接解
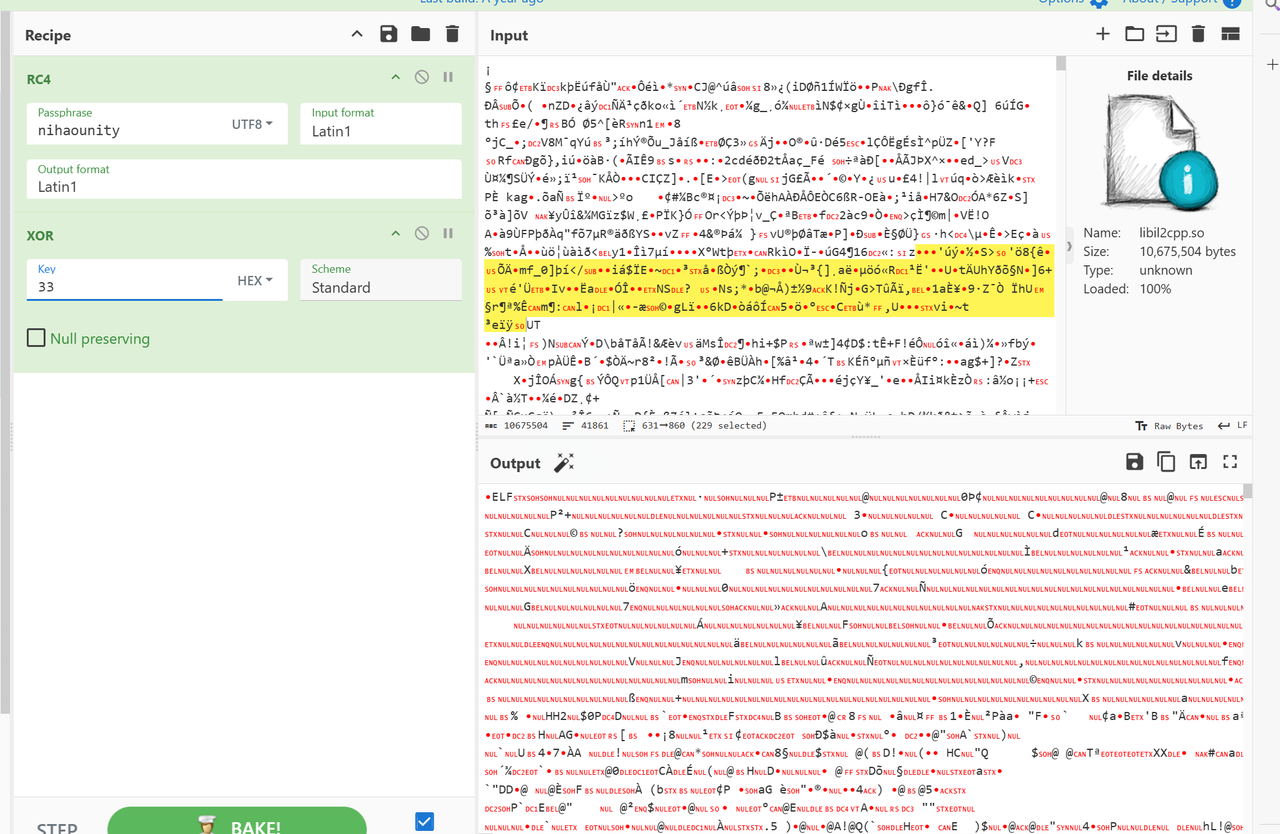
然后是global-metadata.dat的部分,打开解密后的libil2cpp.so进行分析
可以通过字符串查找定位到加载global-metadata.dat的部分
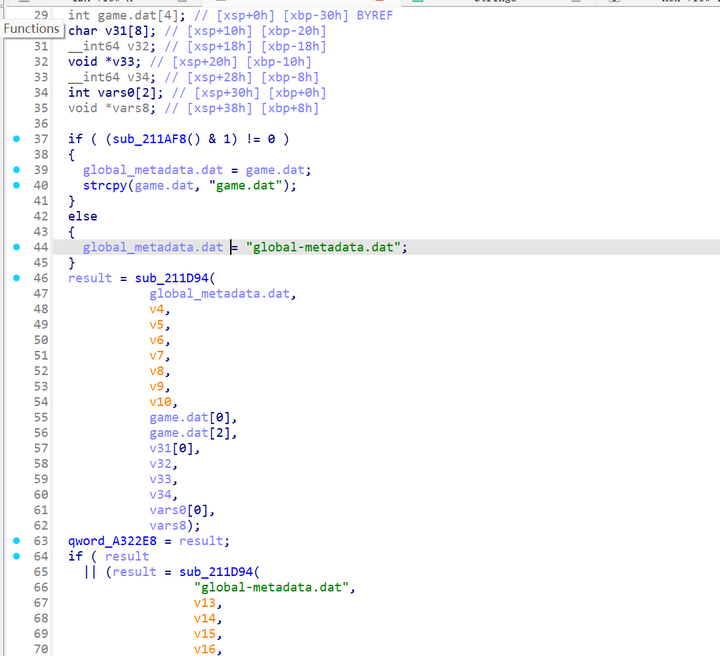
跟进sub_211D94

https://www.bilibili.com/opus/1126494768452337668
这边和标准源码编译出来il2cpp对比可找出解密函数的部分


这里我本来是想继续hook直接dump的,但算法不复杂还是直接扔给ai帮忙了
1 |
|
都解密出来后就可以Il2CppDumper一键梭哈了

后面主要就是对FlagChecker类进行分析
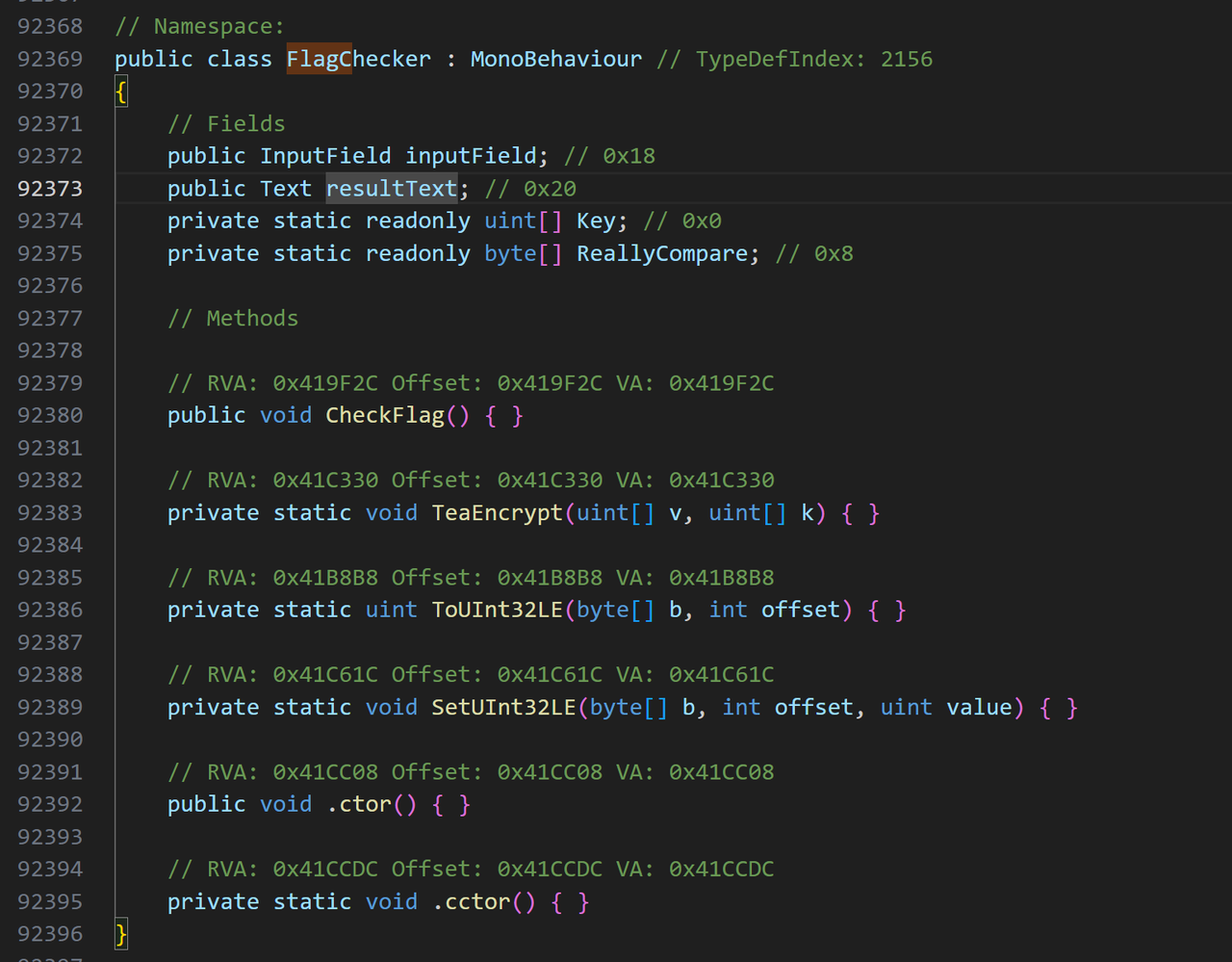
用的是纯原生frida的进行Hook,所以一下数据结构需要自己解析,这边hook了一些关键的数据转换函数
最后给出完整的frida脚本
1 | function hook_il2cpp() |
最后就是一个tea的魔改

byte[]对象的地址,偏移24字节的qword是size,偏移32自己的两处是byte[]结构对应的数据体
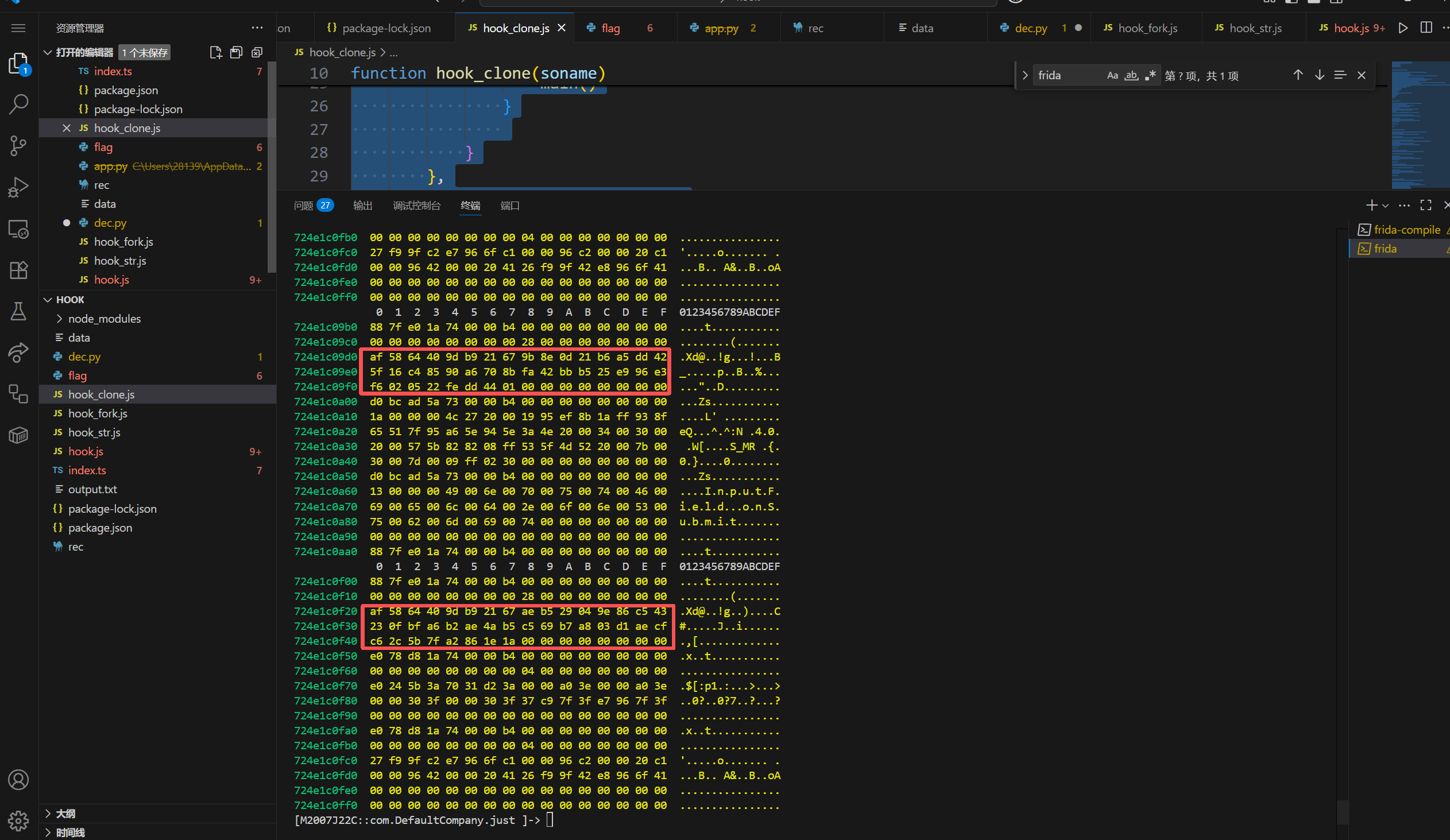
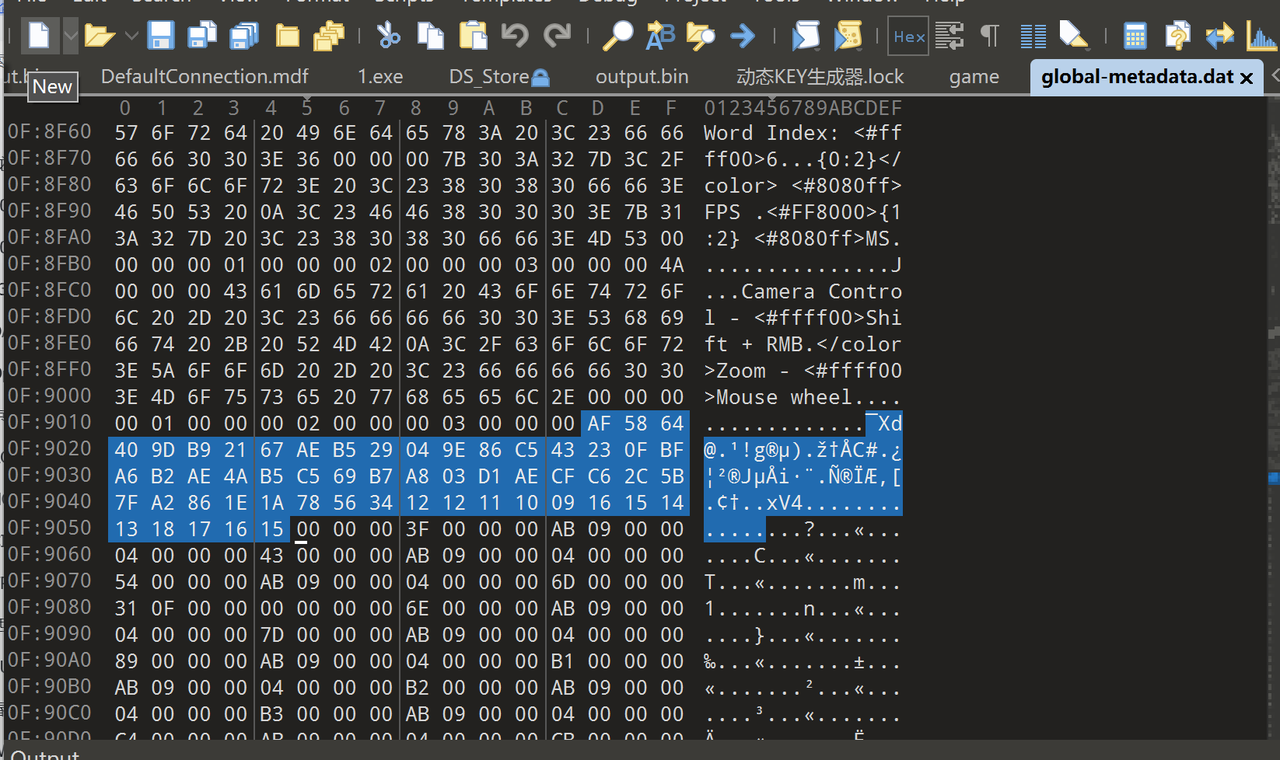
当然这里key和密文也是可以直接静态提取的
找到其构造函数cctor后,获取这串哈希
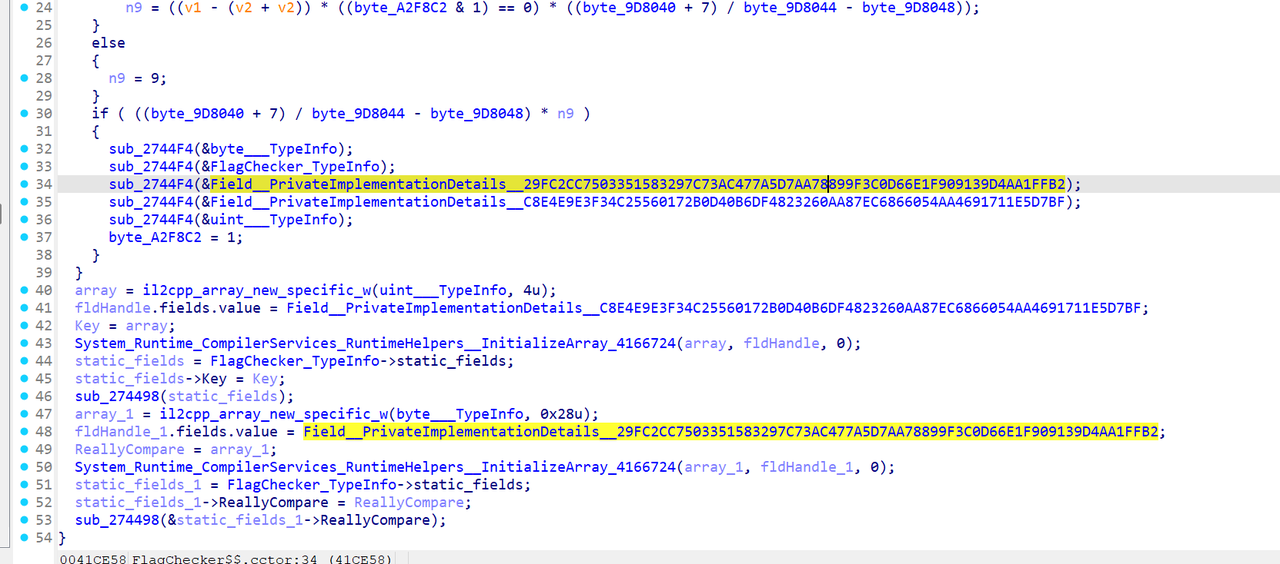
可以在dump.cs中找到这串哈希在global-metadata.dat中的偏移和大小
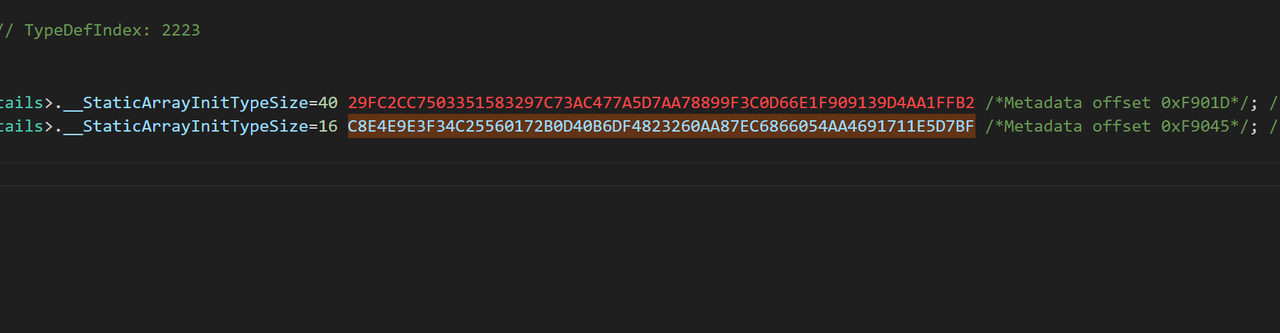
直接提取出密文和key
最终的exp
1 |
|
(最后还是小小地吐槽一下这个UI

- 标题: 强网拟态2025初赛 Mobile方向just Writeup
- 作者: 两只羊
- 创建于 : 2025-10-27 09:44:03
- 更新于 : 2025-10-27 09:48:07
- 链接: https://twogoat.github.io/2025/10/27/强网拟态2025初赛-Mobile方向just-Writeup/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
